Image Credit: Cloud360 Training
In today’s data-driven world, organizations are under increasing pressure to safeguard sensitive data — not just from external threats but also from internal exposure. One simple yet powerful feature in Microsoft Azure helps you achieve this: Dynamic Data Masking (DDM) in Azure SQL Database.
This article walks you through what DDM is, how it works, its use cases, and how you can implement it quickly to enhance your database security.
What is Dynamic Data Masking (DDM)?
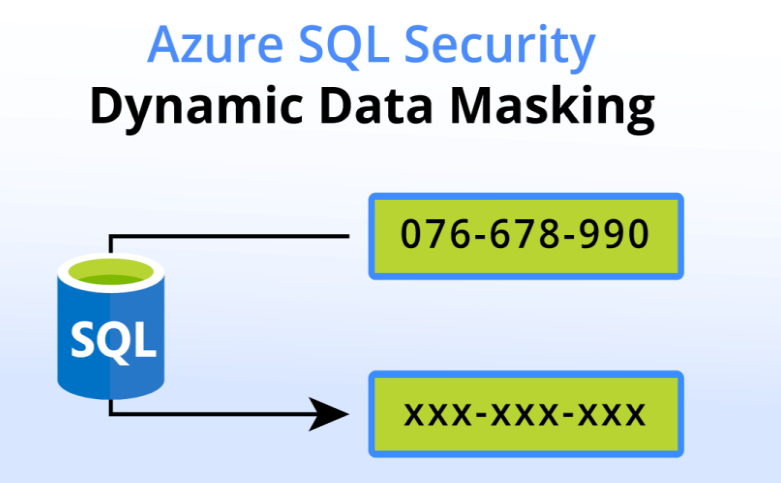
Dynamic Data Masking is a security feature in Azure SQL that limits sensitive data exposure by masking data on-the-fly to non-privileged users.
Rather than changing or encrypting the data itself, DDM modifies the data output at query time, providing a masked version to unauthorized users while allowing full access for authorized roles.
Key Benefits
How Does It Work?
When a user queries a table with masked columns:
For example:
sql
CopyEdit
SELECT Email FROM Customers;
May return:
css
CopyEdit
xxxx@xxxx.com
Instead of:
css
CopyEdit
john.doe@example.com
Built-in Masking Functions
Azure SQL supports several masking functions you can apply at the column level:
|
Function
|
Description
|
Example Output
|
|
default()
|
Full masking with generic values
|
XXXX, 0000, 01-01-1900
|
|
email()
|
Partially masks email addresses
|
jXXX@XXXX.com
|
|
partial(prefix, padding, suffix)
|
Masks part of the string
|
ABXXXXCD (with prefix AB and suffix CD)
|
|
random(start, end)
|
Replaces numeric data with random number
|
Any value between start–end
|
How to Configure Dynamic Data Masking
Step 1: Add Mask to Column
sql
CopyEdit
ALTER TABLE Employees
ALTER COLUMN SSN ADD MASKED WITH (FUNCTION = 'default()');
Step 2: Restrict Access
Remove UNMASK permission from users who should not see full data:
sql
CopyEdit
REVOKE UNMASK ON DATABASE::YourDB FROM [UserOrRole];
Users will now see only the masked data when querying that column.
Real-World Use Cases
Security Note
While DDM enhances data privacy, it is not a substitute for encryption or row-level security. It’s best used as a complementary layer in a multi-layered data protection strategy.
Enable DDM from Azure Portal
You can also configure DDM using the Azure Portal:
-
Navigate to your Azure SQL Database
-
Go to Dynamic Data Masking under Security
-
Select columns and apply the desired masking functions
-
Save and test queries from restricted users
Sample Table with Masking
sql
CopyEdit
CREATE TABLE Customers (
ID INT IDENTITY,
Name NVARCHAR(100) MASKED WITH (FUNCTION = 'default()'),
Email NVARCHAR(100) MASKED WITH (FUNCTION = 'email()'),
CreditCard NVARCHAR(20) MASKED WITH (FUNCTION = 'partial(0,"XXXX-XXXX-XXXX-",4)')
);
Summary
|
Feature
|
Description
|
|
Configuration Level
|
Column-level, easy to apply
|
|
Data Modification
|
No change to actual data
|
|
Performance Impact
|
Minimal
|
|
Access Control
|
Based on UNMASK permission
|
|
Best For
|
Quick data obfuscation for sensitive fields
|
Additional Resources
Final Thoughts
Dynamic Data Masking is a lightweight, effective feature for improving your data security posture. It’s ideal for organizations that need to balance data accessibility and compliance. While it won’t replace strong encryption or full security controls, it’s an excellent first line of defense for sensitive data exposure.
Need help securing your data with Azure SQL?
Contact Cloud360 for expert consulting on cloud security, compliance, and database hardening.