Image Credit: Microsoft
As data security continues to take center stage, organizations using Azure SQL Database need robust protection to guard against unauthorized access. One of the most effective ways to secure data at rest is through Transparent Data Encryption (TDE).
TDE helps ensure your data is protected — even if someone gains access to your underlying storage. This article breaks down what TDE is, how it works in Azure SQL, and how to implement and manage it effectively.
What is Transparent Data Encryption (TDE)?
Transparent Data Encryption (TDE) is a feature in Azure SQL Database and SQL Server that encrypts the storage of an entire database — including data files, log files, and backups — without requiring changes to application code.
It’s called “transparent” because:
Why Use TDE?
How Does TDE Work?
TDE uses encryption keys to encrypt/decrypt data:
Key Components:
|
Component
|
Description
|
|
Database Encryption Key (DEK)
|
A symmetric key used to encrypt the database
|
|
TDE Protector
|
An asymmetric key used to protect the DEK
|
|
Azure Key Vault (optional)
|
A managed HSM or software-based key store
|
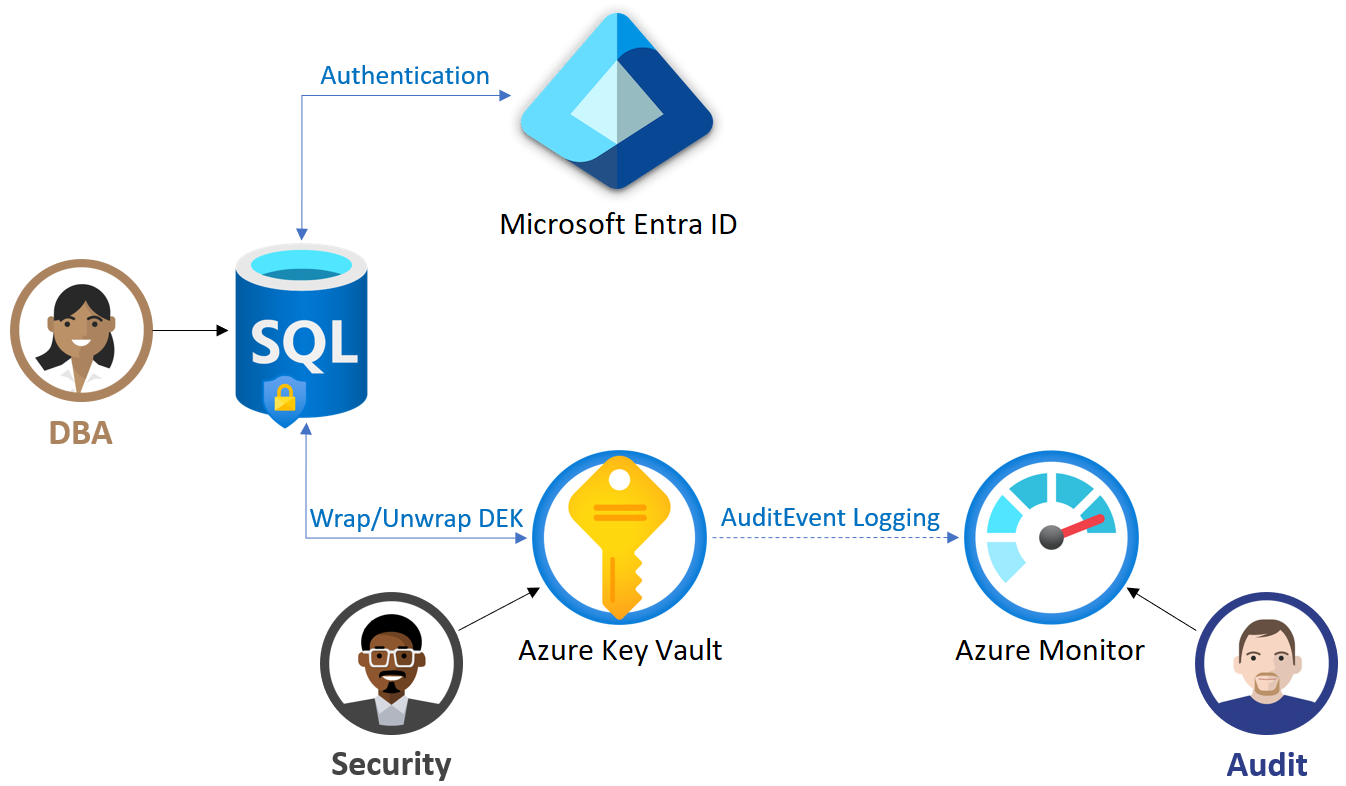
In Azure SQL, the DEK is encrypted using a TDE protector stored in Azure Key Vault (customer-managed key) or Microsoft-managed keys by default.
TDE Options in Azure SQL
|
Option
|
Description
|
|
Service-managed key (default)
|
Azure manages the TDE protector key
|
|
Customer-managed key (CMK)
|
You manage and rotate keys using Azure Key Vault
|
How to Enable or Configure TDE
Option 1: Using Azure Portal
- Navigate to your Azure SQL Database or SQL Managed Instance
- Under Security, go to Transparent Data Encryption
- TDE is enabled by default
- For customer-managed keys:
- Link a Key Vault
- Select the key you created
- Assign appropriate permissions
Option 2: Using PowerShell
Set-AzSqlDatabaseTransparentDataEncryption `
-ResourceGroupName "myResourceGroup" `
-ServerName "mySqlServer" `
-DatabaseName "myDatabase" `
-State "Enabled"
Customer-Managed Key (CMK) - BYOK Scenario
If your organization needs more control over encryption keys:
Benefits of CMK:
Auditing & Monitoring TDE
Important Considerations
TDE on Azure SQL Managed Instance & SQL Server on Azure VM
Summary
|
Feature
|
Description
|
|
Purpose
|
Encrypt data at rest in Azure SQL
|
|
Default Status
|
Enabled by default (service-managed key)
|
|
Optional Feature
|
Use Customer-Managed Key via Key Vault
|
|
Impact on Apps
|
Transparent (no code change)
|
|
Performance Overhead
|
Minimal (typically < 5%)
|
|
Compliance Support
|
Helps meet security standards and regulations
|
Final Thoughts
Transparent Data Encryption is one of the easiest and most effective tools to secure data in Azure SQL. Whether you're handling financial records, healthcare data, or personal customer information, TDE ensures that data stored in your databases is always encrypted, always protected.
To enhance your security posture further, consider pairing TDE with:
Additonal Resources
Want help setting up TDE or managing your own encryption keys?
Contact Cloud360 for expert Azure security consulting and implementation support.